Application, Infrastructure, and Social: An Integrated Approach to Penetration Testing

Aditya Jayanthi
August 16, 2023


Costs of data breaches due to cyber-attacks have continued to climb. In 2023, the global average cost of a data breach has reached USD 4.45M, according to the latest ‘Cost of Data Breach Report 2023’ by IBM Security. This is an increase of USD 100,000 YoY. Whilst this may not come as a surprise to most IT and Security teams, it does highlight the importance of maintaining IT security hygiene.
Penetration testing is the most potent tool to detect and verify the exploitability of vulnerabilities in IT systems. However, the traditional approach to pen testing has been to perform it by either type (Black-box, White-box, or Grey-box) and by asset type (Web Application, Network, Infrastructure, or Social). Sometimes, pen testing service providers do use a combination of techniques to try and compromise a system, but oftentimes the terms of engagement are scoped narrowly to ensure the manageability of testing or as an exercise to tick the box on a regulatory requirement of periodic pen testing. Adversaries do not have such boundaries and will freely use any available attack vector to breach a system.
One of the key findings from the aforementioned report is around the cost and frequency of breach by initial attack vector as shown in the graph below.
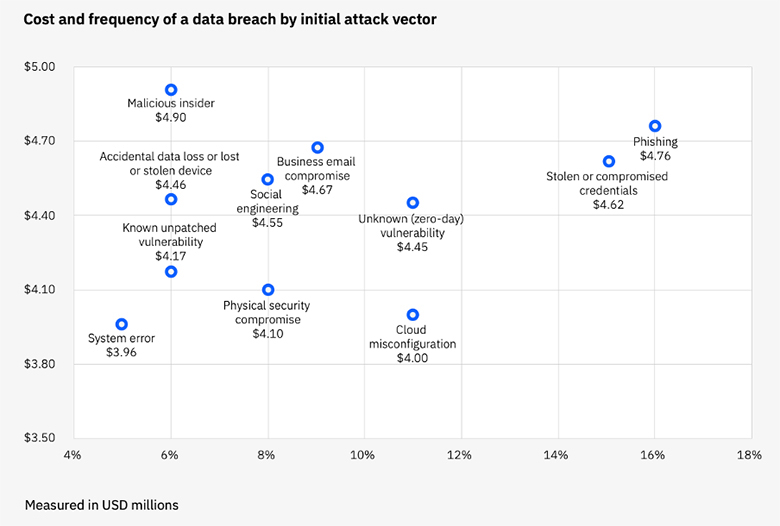
Whilst phishing and stolen/compromised credentials remain the most frequently used attack vectors, cloud misconfiguration has become an increasingly used attack vector, on par with zero-day vulnerabilities. Yet, most pen testing exercises remain focused on web application or API testing (dynamic testing) with source-code security assessments (static testing). Cloud configuration assessments continue to be stand-alone exercises using CSPM tools and with findings often addressed by central cloud ops teams that lack application contexts.
An effective penetration testing exercise needs an integrated approach that starts with the context of the application. It should consider not only the source code of the application using static and dynamic testing but also consider the infrastructure including the compute, network, and storage used for that specific application. With the acceleration of cloud adoption, application infrastructure has also become a piece of code that should be assessed in conjunction with the application source code using the same static and dynamic techniques. Bringing the context of an application to the infrastructure layer helps complete the picture and bring it closer to an adversaries’ view.
This leaves the social part of the equation. Phishing and stolen/compromised credentials remain the most frequent attack vectors used by adversaries. Testing social behaviors requires social techniques such as phishing campaigns, but the effectiveness of these exercises has long been debated. Whilst we do need to continue these exercises, with the increasing prevalence of CI/CD pipelines and everything-as-code, compromising access credentials is a single step away for an (un)intentional developer. Including rigorous checks along each step of the CI/CD pipeline and continuous scanning of code repositories is essential to mitigate the risk of stolen/compromised credentials.
At letsbloom, we have built our platform to use application/workload as a core unit when providing continuous observability and manageability of security and compliance posture. We continuously monitor for security and compliance posture changes in near real-time across the lifecycle from infrastructure-as-code to running cloud resources. Both blue team (defenders) and red team (pen testers) can use this context to get a holistic picture of the cyber security posture of an application and to better detect, analyze, and protect IT systems.
Contact us to find out how we can help you get the most out of your pen testing efforts and improve your security and compliance.










